Mini Guide On How To Use A Check Point Smart Event
In this article, we want to talk about the Check Point SmartEvent product. This product complements and expands the capabilities of the Check Point firewall, turning it into an effective tool that helps identify, recognize and process security incidents. Let’s continue this topic and see how the Smart Event blade is arranged.
Check Point’s software blades generate a huge variety of messages that are stored in the log database. Most of them are messages about allowed and blocked connections, less often – messages about the protection of IPS and other blades of the product. The information stored in the form of logs can be used to study and analyze security incidents, but it is extremely difficult to quickly identify log-based incidents. First of all, because there are a lot of these logs. You can certainly use filtering mechanisms, but you need to know that different logs are important for filtering out and detecting for different incidents. The output can be the automation of the log analysis process. SmartEvent solves the problem of automating log analysis for the purpose of identifying security incidents.
Product Architecture
Let’s look at the parts of the SmartEvent product and what functions these parts perform:
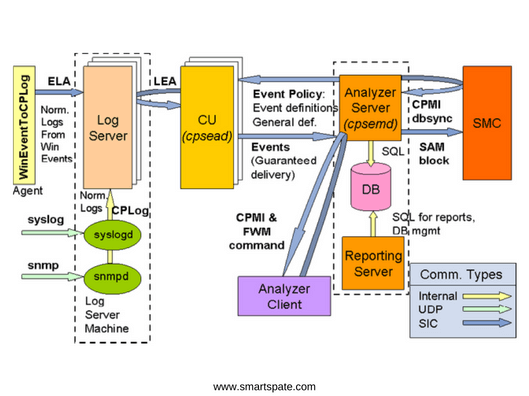
The log server collects logs from various sources.
Correlation Unit (CU) – Reads in real time the records from the current log file of the Log server and analyzes them using the Correlation Policy, generating security events that it sends to the Event Server.
Analyzer Server – Loads the Event Policy policy onto the Correlation Unit, saves the security events received from the Correlation Unit in its database, interacts with the Security Management Server to block the source of the threat on the Check Point security gateways. Loads the necessary objects from the Security Management Server. Provides data for the generation of Reporting Server reports.
Analyzer Client – Organizes interaction and management interface with Event Server, displays information collected on Event Server in various views.
All these three parts of the product can be deployed on the same hardware module and at different. You can purchase SmartEvent both as a software blade and as an application (Smart-1 SmartEvent).
Event Policy
SmartEvent immediately after deployment has a set of built-in policies sufficient to detect a large number of security events. The politicians are grouped together.
To open the list of Event Policy for version R80.10, in the SmartConsole under Logs & Monitor, open a new tab and select SmartEvent Settings & Policy at the bottom of the window. A new window opens with a list of policies. Active policies will be marked with a tick.

To view the settings of the policy you are interested in, right-click on the policy and select Properties.
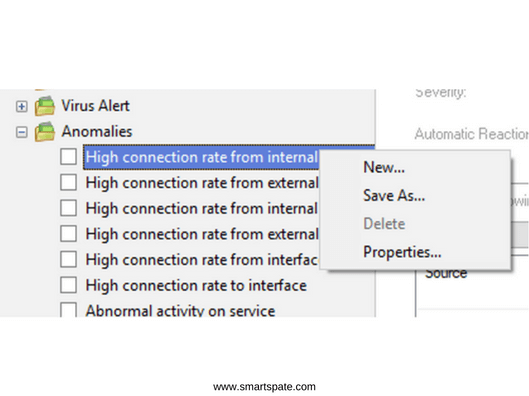
The policy has five property tabs. The first tab (Name) specifies the name and description of the policy, as well as the level of importance of the security event generated by the policy.

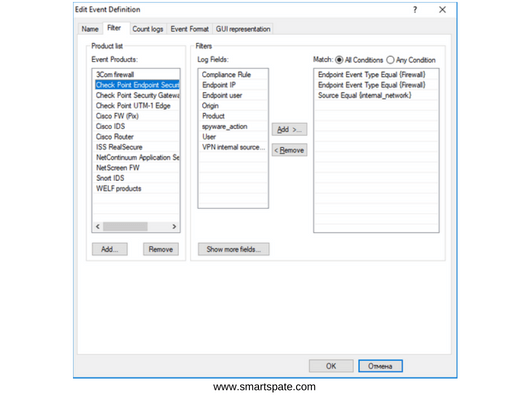
The second tab (Filter) of the policy properties sets a filter for log entries. Each Event Products corresponds to a certain set of fields, filled with this product in the log file. A filter is formed on these fields. For example, in our policy “High connection rate from internal hosts on service” for the Check Point Endpoint Security product, log records are perceived, in which the Source IP address belongs to the address space from internal networks.
The third tab (Count Logs) configures the criteria for generating a security event. In the policy we are considering, a security event with a Medium severity level will be generated if 200 calls are detected within the same service/protocol between a pair of IP addresses within 60 seconds.

The Event Format tab determines which significant fields will be in the security event message and the values of which fields from the log file will be recorded in them.

On the GUI Representation tab, the Threshold, Exclude, and Exception sections of the policy section are configured.

How these sections look at the policy description:
- Threshold
- Exclude
- Exception

Tuning Event Policy
As a rule, Event Policy policies require “tuning” in order to eliminate erroneous operations and improve the accuracy of work. Tuning is to configure policy settings and add exceptions. Exceptions are of two types:
- Exclusion – sets the parameters of logs (for the policy we are considering is Source, Destination, Service) which the policy will not perceive in its work.
- Exception – Specific security events that will be ignored by the policy.
You can also set an automatic response for each policy. The reaction can be the commission of a set of actions, including:
- Sending an email message
- SNMP Trap
- Source IP Blocking
- Blocking activity (Block Event activity)
- Executing an external script.
We hope this article will help you better understand the right product, like Check Point SmartEvent.





