Critical Vulnerability In Gmail That Allows Intruders To Bypass It Through The FireFox
Recently, Google introduced a new design for Gmail. If desired, each user can go to it, and soon all users of G Suite will be forcibly transferred.
In this design, several new security features are implemented, including the so-called confidential mode. Here the sender sets the validity period of the letter, after which it “disappears”. At least that’s how it should work. In fact, there are several ways to bypass this protection, save the received message, copy or print it.
Google calls this system Information Rights Management – a term more than ten years ago invented by Microsoft for a similar function in Microsoft Office. In reality, this is a kind of DRM analog, only for e-mail.
Experts from the Electronic Frontier Foundation see several problems in the way the Gmail privacy mode is implemented.
Non-serious protection
- First, these are simple methods of circumventing this “defense”. Obviously, you can make a screenshot of the received letter. You can simply save it in its original form. Although Gmail does not have a “Save” or “Download a letter” button, in the browser, there is such a button and it works fine on confidential emails.
- Secondly, the message is not actually deleted completely – it continues to be stored in the “Sent” folder of the sender, that is, on the Google servers. Even if both the sender and the recipient clicked the “Delete Forever” button and cleaned the Recycle Bin, the messages still remain on Google servers for up to 60 days.
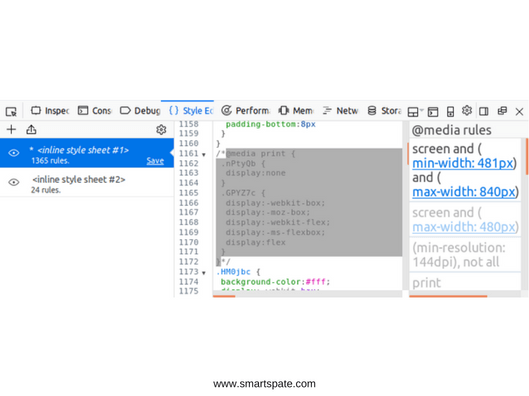
Finally, Google prohibits the printing of confidential messages from the web interface. But such protection is implemented using CSS rules @media print, which hide the main content at the time of printing. It is very easy to remove the ban on printing. For example, in Firefox, open the Style Editor in the Web console-and remove unnecessary rules. Alternatively, you can just click on the left icon in the shape of the eye – and turn off all the CSS styles on the page. In other browsers with built-in developer tools, you can also find @media print in the code, comment out it, or delete it. But in Firefox, this is done, perhaps, the easiest.
- In general, @media print rules are implemented in the standard in order to help the user to print the page without unnecessary “garbage”. That is, Google uses this rule, not for its intended purpose and abuses it, experts say.
Google also used several tricks to block the copy-paste, but they can also be circumvented.
First, this CSS property is user-select, which does not allow you to select text. It is deactivated from the same style editor in Firefox: it’s enough just to disable all styles or write your own rule, which returns normal behavior (auto) when selecting text.
Secondly, Google has implemented JavaScript, which blocks the context menu, which allows you to copy the text. This restriction in Firefox is removed in the configuration about config, where the setting of dom.event.contextmenu.enabled should be set to false (false means that JavaScript does not have the ability to block the context menu).
Illusion of safety

We can assume that even such unreliable protection of letters is better than none at all. Unfortunately, it is not. Experts on information security have repeatedly warned that in such conditions, users have the illusion of security. Because of this, they are more careless about the transfer of confidential information, relying too much on the security and privacy of Gmail messages. In other words, such protection can even worsen the real protection of information and increase the number of leaks of confidential documents.
“If money, if the market determines security measures and if people make decisions based on a sense of security, then the smartest thing a company can do, based on economic considerations, is to give people a sense of security. And there are always two ways to achieve this. The first is to really protect people and hope that they will pay attention. Or the second – you can create a sense of security and hope that they will not pay attention, “- said Bruce Schneier in his lecture TED, which is called “The Illusion of Security.”
DRM in the mail
EFF experts note that confidential mode does not use end-to-end encryption, that is, the email still runs in clear form through Google’s servers, and the company has the technical ability to store copies of letters for an unlimited time, regardless of the “delete date”.
- In addition, to activate protection by an SMS code, the sender must disclose the Google mobile number of the recipient’s mobile phone – potentially without the consent of the recipient.
According to EFF, the IRM (DRM) system implemented in Gmail relies not on technology, but on the Digital Millennium Copyright Act (DMCA) of 1998, which explicitly prohibits third parties from circumventing this protection. For the first such violation, up to five years’ imprisonment and a fine of up to $ 500 thousand are threatened. Theoretically, disabling protection in the Firefox Web console style editor can also be considered a violation of the DMCA. Again, theoretically, Google has the right to pressure Firefox developers to deactivate this feature for Gmail and begin to pursue developers of third-party extensions that will try to return this functionality to Firefox.
“We believe that products for information security should not rely on the courts to secure their intended guarantees, but must rely on technologies such as end-to-end encryption that provide actual mathematical guarantees of confidentiality,” the EFF said. “We believe that the use of the term” confidential mode “for a function that does not provide confidentiality, as this term is understood in IB, is misleading.”
EFF believes that there can be no confidentiality in the unencrypted mail, this also applies to “confidential mode” of Gmail. Perhaps this function makes sense in a narrow corporate environment, but for most users, it does not guarantee privacy and the necessary functions inherent in secure communications. First of all, there is no reliable end-to-end encryption of mail with a digital signature.