Security Weekly 22: Accenture Laid Out Everything On Amazon, A Year Of Malware On Pornhub, A Fresh Attack On MS Office
We do not know how to live without cloud technologies, but we have not learned to live with them yet. Every now and then ridiculous mistakes happen because people do not really understand that their cloud resource and a similar local one are two big differences, and you need to handle them accordingly.
- For example, as now, when the researchers found in Amazon S3 a large clearing with tasty data, kindly covered by the company Accenture.
The company is engaged in consulting, helps clients strategically plan, optimize, modernize and implement. They work with the world’s largest corporations, which earns about $ 5 billion a year, slightly smaller than Gazprom.
- And this consulting giant in the Amazon S3 had four baskets open out even without a password. You know the URL – go in, unload what you want.
The baskets were full of Accenture customer data. Detecting them folks from UpGuard did everything right – told the data owner, waited until all this is removed from the access, after which they already with a clear conscience published a report on the find.
- The participants themselves hastened to state that nothing terrible had happened: they had a multi-level security model, and these data would not have helped hackers to overcome any of the levels. Well, you know, they are security models like onions – they have many layers.
The Truth is if you read into the report, it seems that the data was still a little bit important. And there were internal access keys and credentials for the Accenture API, private Accenture signs keys, an Accenture account key for Key Management Service in Amazon Web Services, database dumps where Accenture client credentials were found, password hashes, and a small a backup with 40 thousand unencrypted passwords. With this information, someone could very well conduct a “man in the middle” attack and stand between Accenture and its unsuspecting customers.
That’s strange – the basket created in S3 is configured by default as private and requires authentication for access from the outside. That is, it turns out that someone has reconfigured these four baskets. The moral of this fable is that the company can be arbitrarily respected, it can have the largest customers, but some interesting person can in four clicks cool everyone.
Pornhub engaged of malware spreading
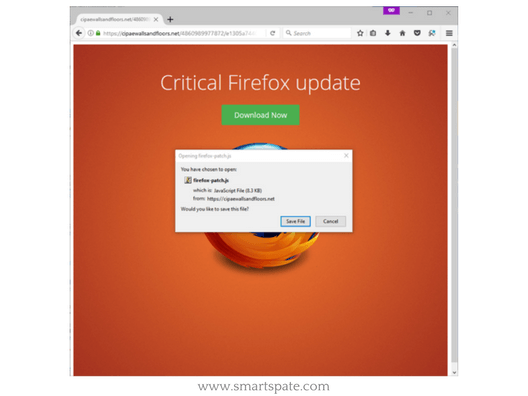
It sounds like a sexual perversion, but there was only another puncture in safety. The largest porn site (according to Alexa ranked 21st place among American sites, among other things) picked up malicious banners from the banner network TrafficJunky and for about a year showed them to visitors.
- Visitors from Pornhub – around 8.7 million a day, that is, a plentiful harvest of campaigners was provided. The victim who clicked on the banner received an offer to update the browser and launched a js-file, which, in turn, downloaded an interesting piece – almost disembodied Kovter Trojan.
Kovter is famous for keeping itself in the Windows registry keys, saving in the file only a script to extract itself from the registry. In this case, the researchers found only a clicker version of Kovter, which is used for fraudulent earnings on non-existent transitions on advertising banners, but earlier in nature, they caught the ransomware option.
Pornhub, so active in social networks and media, did not comment on such an outstanding failure, but it is possible to predict with certainty that this incident will not affect the number of visitors. Visitors to porn sites either take risks or ignore it – you can not hide the libido in your pocket!
Microsoft patch actively exploited flaw in Office

A news that provokes a keen sense of déjà vu. The most popular office suite in the world is doomed to the attention of hackers, and often they manage to get ahead of researchers, finding vulnerabilities before. Sometimes – much earlier.
- Researchers from Qihoo 360 Core Security in late September, discovered a new, with a need, an attack on their customers, during which valuable information leaked from computers. After the analysis, it turned out that the tools of the attack had been developed somewhere in August, that is, a month or two hackers were free to visit Office users as to their dacha.
Vulnerability CVE-2017-11826 is relevant for all supported versions of Office. Malicious .docx was built into RTF files, you have to try to open it to infect it – in order to force the victim to do this, the attackers used the old kind social engineering. Correctly using tags in a Microsoft Word document, attackers achieved execution of malicious code with the rights of the current user.
Especially the attack is fraught with the fans to work with administrator rights – in this case, an attacker can install programs, view, modify or delete data, create new accounts with full rights. Microsoft closed the issue on its Tuesday patches, along with 62 other holes.





