Security Weekly 43: Cryptic Hysteria In The Exchange Of Encrypted Messages
It was a difficult week for the means of exchanging encrypted messages. The funds seemed to work, but in one they will find a hole, then in another, what a problem.
It all began on Monday when a group of European researchers announced serious vulnerabilities in a number of mail clients that support OpenPGP or S / MIME encryption (news). Announced, shared information with the most important people “under the embargo”: in a world of vulnerabilities, they do it so that the vendors that have come under the distribution can, for example, issue a patch. And also – that “especially important people” speak in favor of the importance and need for research in public.
- But something went wrong, and instead of Tuesday had to publish information on the same Monday (apparently, the discussion went on Twitter and details began to be revealed). For two published scenarios of attack, the presence of its brand (Efail), logo and web page looks strange, but, alright, okay. Both methods of attack exploit the message viewer built into email clients as web pages. In the message, before the encrypted text, a broken img tag is inserted – so that not only the request to download the image goes to the attacker’s server, but that the decrypted message is still attached to it.
The first method of attack uses a very simple scheme when the “poisoned” tag is inserted in the clear text. In the second, everything happens a little trickier: the lack of integrity checks is exploited in the same S/MIME (OpenPGP is vulnerable but to a lesser extent), so a similar “malicious” tag can be inserted directly into the encrypted text.
Video demonstration of an attack
That is, an attacker must not only gain access to the victim’s encrypted messages. He will have to modify them, send back the victim and hope that on the other side the built-in “beacon” will work. Not the most effective method, but, on the other hand, it’s about encryption, and in encryption, the level of paranoia everyone chooses for themselves. It is also interesting that the EFF fund’s reaction was not quite adequate: on Monday, having read the report under the embargo, they wrote that “this is a very serious problem,” and recommended that everyone-everyone-switch to Signal. After the release of the full report, details were retold at the EFF site, but the recommendation to install Signal (and still remove the plugins for decryption) remained.
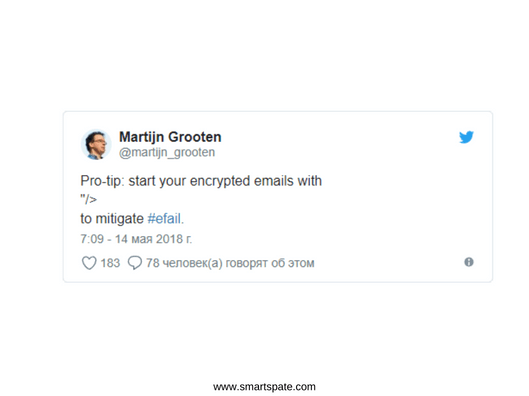
About “remove the plugins” and “do not decrypt already received messages”: in the case of Efail there is a temporary solution (before the release of the patch for the email client you are using) it’s much easier: turn off the HMTL-presentation of messages. In the playtest, the attack is obviously powerless. And about Signal: it is not very clear the desire of EFF to advertise this messenger about and without reason, especially since the change of infrastructure (mail -> chatic) like this, from one small problem, should not occur.
Signal also found a problem, and also not the most terrible in the world. Researchers found in the desktop version of the messenger an excessively free treatment of HTML-codes, which allows you to conduct an XSS-attack and generally can in every way mislead users. The problem was first patched, but then it turned out – not until the end. And for the Telegram messenger (more precisely, for its desktop version), the Trojan Telegrab was discovered, stealing the history of the victims’ messages and adding it to the server with open access. In difficult times we live!





