Security Weekly 46: The Secret Of Non-Trivial Cyberattacks
Imagine that the bright future of information technology has come. Technologies for code development have been developed and widely implemented. The most common software is extremely difficult to crack, and it makes no sense: the most interesting data is generally stored in a separate, fully isolated firmware “safe”.
- Hack someone’s mail by picking up a simple password, to use tightly “wired” admin access to the router is no longer possible: the practice of developing and qualitative audit of the combined capabilities of such “simple” vulnerabilities almost to zero.
Will this (unlikely) scenario end the cyber attacks? Hardly, they will just become more expensive. Nontrivial methods of hacking, which are currently simply not needed (there are ways to get the necessary information much easier), will be in demand. The same Specter is, after all, a set of vulnerabilities, which are extremely difficult to use for something really useful harmful. But if there is no choice, such methods will do. Today – two fresh examples of non-trivial attacks: acoustic DoS hard drives and stealing pictures from Facebook via CSS.
Sound and ultrasonic attacks can disable hard disks and “suspend” software
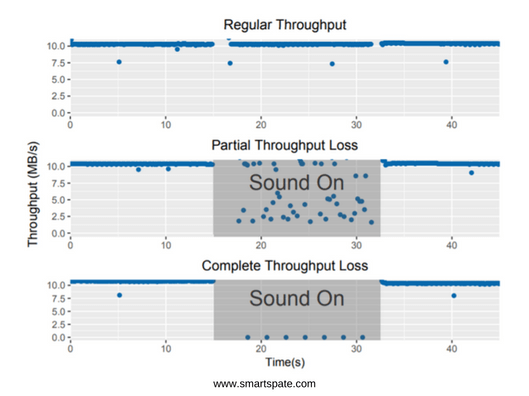
Researchers from the Zhejiang University in China and the American University of Michigan have shown how you can disable computers with the help of sound and ultrasound signals. Blame all the usual hard disks, badly transferring not only impacts but also various kinds of vibration, including acoustic signals. The picture from the study clearly explains everything:
From the top – the normal operation of the hard drive, in the center – we begin to “irradiate” the sound of medium volume, the data transfer rate drops. Bottom: a major disruption in the operation of the hard drive. All would be ok, but the DoS attack is “reliable” (on the lower chart) implemented at a volume of 117 dB SPL, while a sinusoidal signal with a frequency of 5 kilohertz is transmitted. This is a very loud attack. But this is fixable: similar results, but already on a laptop 2.5-inch hard drive was achieved by transmitting an ultrasonic signal at a frequency of 31.5 kilohertz.
The authors of the study at the 39th IEEE on Security and Privacy Symposium
In the study, an example of an attack on a laptop is given, with the dynamics of the attacked device becoming the source of the attack: 45 seconds of howls of a specially formed acoustic signal, and a blue screen is obtained. I’m not sure that this is a realistic scenario: the further, the harder it is to find devices with a traditional HDD instead of a solid-state drive. But the scenario of the attack on the video surveillance system is quite realistic: there will be a lot of hard drives for a long time to come. Researchers have achieved a short break in the record after 12 seconds of attack on a real surveillance system. A 105-second attack takes the system completely out of service, until the next reboot. So I imagine the arsenal of cyber-savvy robbers of the future: suckers for moving around the walls of expensive office buildings, and a column to yell at the video cameras to their full inoperability.
Theft of the user’s personal data through an error in the implementation of CSS
- News
Researcher Ruslan Khabalov, a security specialist at Google, together with an independent expert Dario Weiser, discovered an interesting bug in the implementation of CSS in Chrome browsers (repaired since version 63) and Firefox (patched in version 60). The attention of researchers was attracted by the mix-blend-mode method, which allows to more organically “enter” one element on top of another – for example, the Facebook widget on top of the background on the website.

The vulnerability lies in the fact that the time required to render a new element depends on the color of the source. In other words, a potential attacker has the opportunity to obtain data, access to which in theory should be prohibited. The proof of concept shows how it is possible to “steal” the name and photo of a user using such indirect data, which is simultaneously logged on Facebook and visits the “prepared page”:
- It works, let’s say, well, very slowly (we must bear in mind that this is PoC, and the author was not interested in optimizing the algorithm). Steal the username from the FB widget in 20 seconds. Rendering a rather soap-topped user pin took as much as 5 minutes. Well, okay, here is the very fact of using a non-trivial data channel, through which information leakage occurs. In the case of this vulnerability, everything seems to be all right: they found it, quickly closed it, and hardly anyone would come up with the idea to use it in practice.
The question is, how many still have “holes” through which important information can leak and which we do not yet know? This is not even about the fact that someday in the future it will come to the practical application of such complex attacks – from despair. The point is that even now they can be implemented in such a way as to completely bypass absolutely all means of protection – because no one expects a blow from the rear. That is why such non-trivial methods of attack through one place, both on hardware and software, are of particular interest.





